In the digital world, user authentication is essential for maintaining secure access to online accounts and resources. User authentication verifies the identity of a user before granting access to sensitive information or systems.
There are many different methods of authenticating users, and each has its own advantages and disadvantages. The most common methods of user authentication are:
- username and password,
- two-factor authentication,
- biometrics just to list a few.
But as time passes we continue to evolve and new methods are introduced that even guarantee a safer way to store user data, good examples of these methods include:
- Passwordless login
- Multifactor authentication, and
- Token-based authentication
In this article, we will explore the most common methods of user authentication and their advantages and disadvantages. By understanding the different options available, you can choose the best method for your needs. But first, let's understand what we mean by Authentication.
What is Authentication?

Authentication is the process of verifying the identity of a user. There are many ways to authenticate a user, each platform has different methods that they use but some common methods include username and password, fingerprint, facial recognition, and iris scan.
A username and password are the most common form of authentication. Whereby a user enters their username and password into a login form, and if the credentials match what is stored in the database, the user is granted access. However, this method can be insecure if passwords are not properly encrypted or if users reuse the same password for multiple accounts.
Fingerprint authentication uses an individual's unique fingerprint to verify their identity. This can be done using a fingerprint scanner or by using a smartphone's built-in sensor.
Facial recognition works in a similar way, using an image of the user's face to verify their identity. Iris scanning is another biometric authentication method that uses an image of the user's iris to identify them.
Even though we have listed this as the most common one, in the recent past year we have seen a rise in other methods which are said to be more secure compared to the ones listed above. As a matter of fact organizations like Google, GitHub, and Microsoft use these techniques in addition to the user providing a username and password, it is considered an extra layer of security, they include:
Two-Factor Authentication
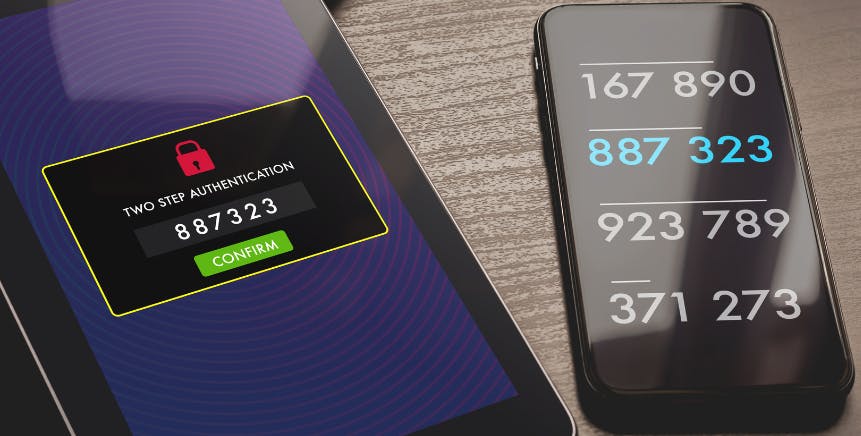
Two-factor authentication, also known as 2FA, is an additional layer of security that can be used to protect your account. When 2FA is enabled, you will be prompted for the second piece of information (usually a code generated by an app on your phone) whenever you try to log in. This makes it much more difficult for someone to gain access to your account, even if they have your password.
2FA is not foolproof, but it is a valuable tool to help keep your account safe. If you are concerned about the security of your account, enabling 2FA will be of great help.
Passwordless Login
There are many reasons why you would want to ditch the password and opt for a passwordless login experience.
For one, it's more convenient for users. They don't have to remember yet another username and password combination. And two, it's more secure. There are no weak passwords to be guessed or brute-forced by attackers.
So how do you set up a passwordless login? There are a few different methods you can use, each with its own set of pros and cons.
One popular method is to use an email link. When the user wants to log in, they provide their email address. They then receive an email with a link that expires after a certain amount of time. When they click the link, they're logged in without having to enter a password.
Another option is to use a one-time code generated by an app on the user's phone. The code is valid for only a short period of time, so even if someone were to intercept it, they wouldn't be able to use it.
Which method is best for you depends on your security needs and preferences. But whatever you choose, ditching the password is sure to make life easier for your users - and make your site more secure in the process.
For a practical guide on how to use the passwordless method Auth0 has a demonstrated step-by-step guide on how to implement this.
Multifactor Authentication
It is also known as MFA. Multi-factor authentication is an authentication method that requires a user to verify their identity by providing more than one piece of information identifying them.
A good example of this authentication is when you set up an online banking system, despite having entered a correct username and password your might be required to either provide your prints or even a code in order for some transaction to happen.
Token-Based Authentication
Token-based authentication is a method of authenticating users that involves providing them with a token. This token can be used to identify the user and provide access to certain resources.
There are many benefits to using token-based authentication, including improved security and scalability. Tokens, while costly and inconvenient at times, they provide a greater level of security than passwords or biometrics since they are only issued.
This method is relatively new and it has become more popular in recent years as web applications have become more complex and distributed across multiple servers. It offers several advantages over other methods.
With token-based authentication, the token is stored on the client side, making it much more secure. In addition, since there's no need to store tokens on the server, scaling becomes much easier.
Overall, token-based authentication offers better security and performance than other methods and if you're looking to implement an auth system for your web application, consider using tokens!
Conclusion
In conclusion, user authentication is a critical part of any web application. It is important to choose an authentication method that is both secure and easy to use. There are many different factors to consider when choosing an authentication method, but the most important thing is to choose one that will protect your users' data.
